How to regain access to an Azure subscription when Owner or any other role was deleted by accident
Step 1: Elevate access for a Global Administrator
Follow these steps to elevate access for a Global Administrator using the Azure portal.
Sign in to the Azure portal as a Global Administrator.
If you are using Microsoft Entra Privileged Identity Management, activate your Global Administrator role assignment.
Open Microsoft Entra ID.
Under Manage, select Properties.
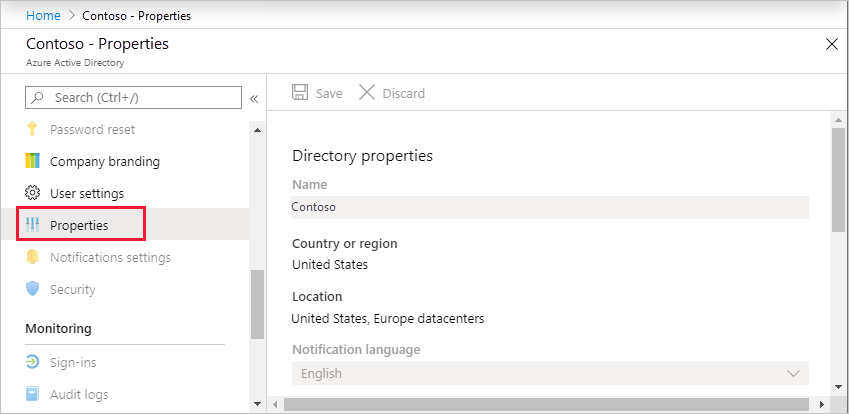
Under Access management for Azure resources, set the toggle to Yes.
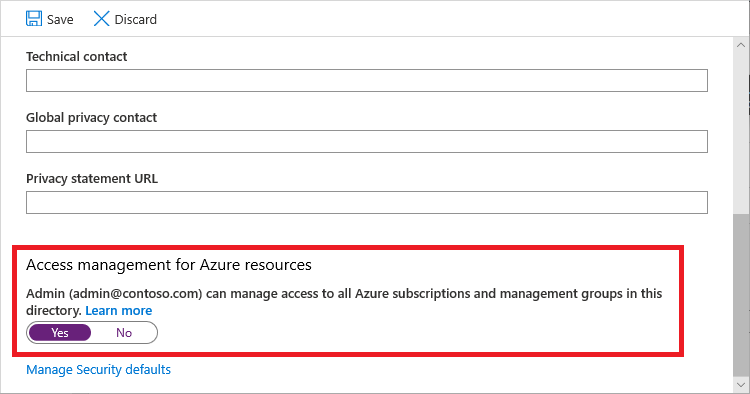
When you set the toggle to Yes, you are assigned the User Access Administrator role in Azure RBAC at root scope (/). This grants you permission to assign roles in all Azure subscriptions and management groups associated with this Microsoft Entra directory. This toggle is only available to users who are assigned the Global Administrator role in Microsoft Entra ID.
When you set the toggle to No, the User Access Administrator role in Azure RBAC is removed from your user account. You can no longer assign roles in all Azure subscriptions and management groups that are associated with this Microsoft Entra directory. You can view and manage only the Azure subscriptions and management groups to which you have been granted access.
Note
If you're using Privileged Identity Management, deactivating your role assignment does not change the Access management for Azure resources toggle to No. To maintain least privileged access, we recommend that you set this toggle to No before you deactivate your role assignment.
Click Save to save your setting.
This setting is not a global property and applies only to the currently signed in user. You can't elevate access for all members of the Global Administrator role.
Sign out and sign back in to refresh your access.
You should now have access to all subscriptions and management groups in your directory. When you view the Access control (IAM) pane, you'll notice that you have been assigned the User Access Administrator role at root scope.
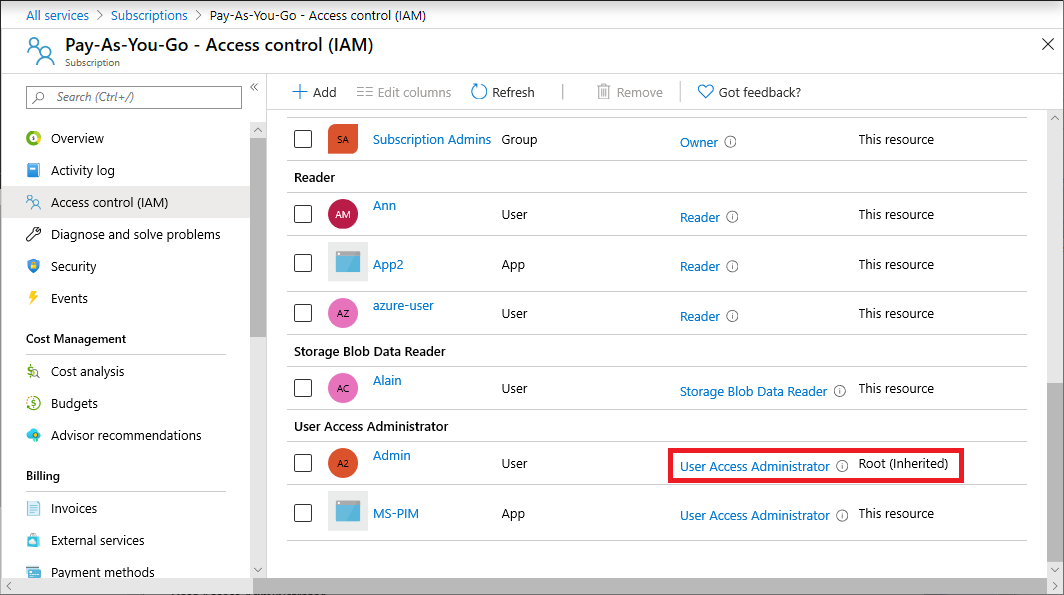
Make the changes you need to make at elevated access.
For information about assigning roles, see Assign Azure roles using the Azure portal. If you are using Privileged Identity Management, see Discover Azure resources to manage or Assign Azure resource roles.
Perform the steps in the following section to remove your elevated access.
Step 2: Remove elevated access
To remove the User Access Administrator role assignment at root scope (/), follow these steps.
Sign in as the same user that was used to elevate access.
In the navigation list, click Microsoft Entra ID and then click Properties.
Set the Access management for Azure resources toggle back to No. Since this is a per-user setting, you must be signed in as the same user as was used to elevate access.
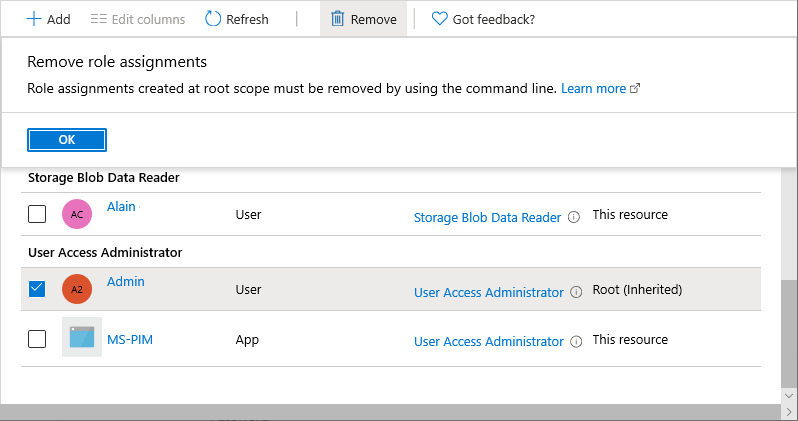
If you try to remove the User Access Administrator role assignment on the Access control (IAM) pane, you'll see the following message. To remove the role assignment, you must set the toggle back to No or use Azure PowerShell, Azure CLI, or the REST API.
Sign out as Global Administrator.
If you are using Privileged Identity Management, deactivate your Global Administrator role assignment.
Note
If you're using Privileged Identity Management, deactivating your role assignment does not change the Access management for Azure resources toggle to No. To maintain least privileged access, we recommend that you set this toggle to No before you deactivate your role assignment.
View elevate access log entries in the Directory Activity logs
When access is elevated, an entry is added to the logs. As a Global Administrator in Microsoft Entra ID, you might want to check when access was elevated and who did it. Elevate access log entries do not appear in the standard activity logs, but instead appear in the Directory Activity logs. This section describes different ways that you can view the elevate access log entries.
View elevate access log entries using the Azure portal
Sign in to the Azure portal as a Global Administrator.
Open Monitor > Activity log.
Change the Activity list to Directory Activity.
Search for the following operation, which signifies the elevate access action.
Assigns the caller to User Access Administrator role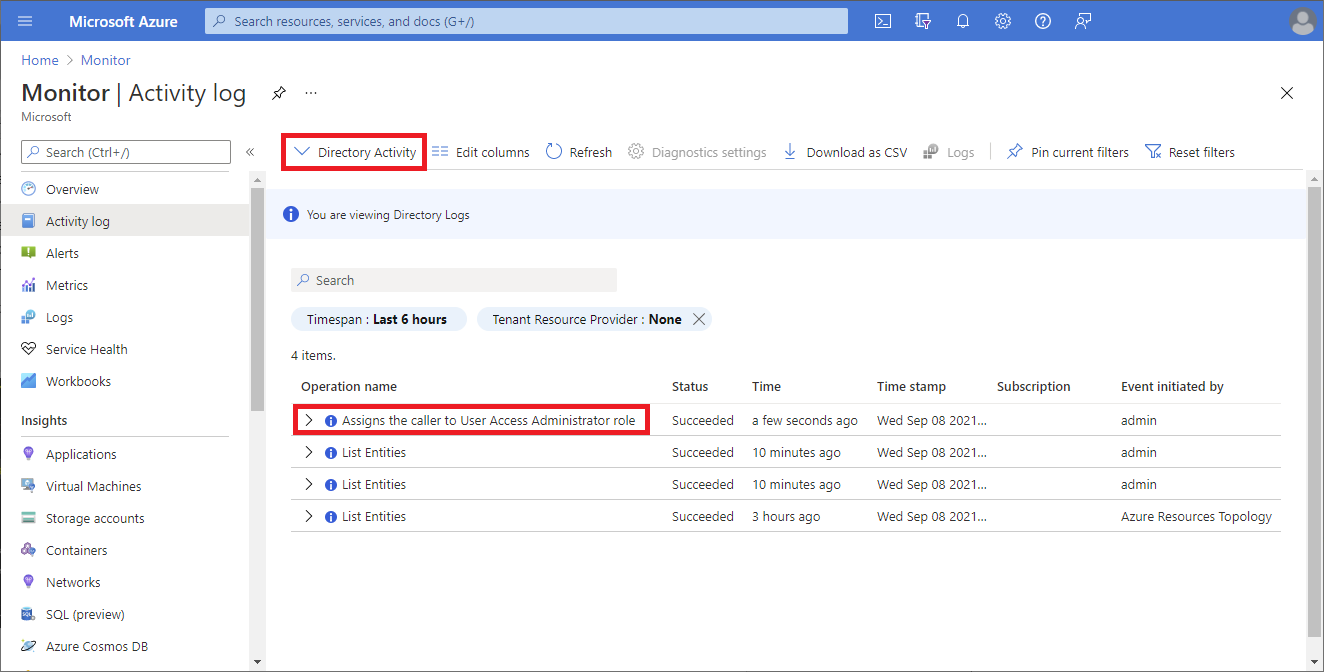
Related Articles
How to log in to your Azure Virtual Desktop (AVD) environment
Voiceware offers Azure Virtual Desktop platform as a service or commonly known as PaaS for its clients. This enables our customers to work from their offices or remotely. This provides you with daily backups of your data and guarantees minimum ...Error with FSLogix service when logging in to Azure Virtual Desktop environment
An error can occur when a new user logs in to the virtual environment for the first time. A window with the following information can be seen depending on the error. ***You need to enable file share access permissions for the FSLogix Files Shares. ...How to deploy RingCentral on an Azure Virtual Deployment (AVD) environment
RingCentral, a telecommunications provider offers the ability to install its desktop app on a Personal Virtual machine or Pooled Desktop environment within Azure Platform. The deployment consists of 3 parts: 1- Install the RingCentral Deployment tool ...Users not able to log in to Azure Virtual Desktop environment after enabling 2 Factor Authentication (2FA)
When enabling 2 Factor Authentication (2FA) or Multi-Factor Authentication (MFA) on a user it can cause the Remote Desktop Client connection to your Azure Virtual Desktop environment to fail with an error "The Logon Attempt Failed" as seen below: ...Error when trying to Subscribe to AVD Resouce using Remote Desktop Service app
The following error occurs since the system is trying to log you in to your tenant but the computer you are using is connected to a different work or personal account. For example: I am logged in to my physical computer with support@voicewareusa.com ...